
Information Technology (IT) Consulting Services
Introducing our premier onsite consulting service designed to elevate your business to new heights. Meet Robin, a seasoned industry expert with over 25 years of invaluable experience in the field. As a trusted consultant, Robin specializes in collaborating with business owners and managers to transform visions into reality.
Why Choose Our Onsite Consult:
Expert Guidance: Robin's extensive industry experience positions him as a valuable asset to your business. His wealth of knowledge enables him to provide insightful guidance, ensuring that your business strategy aligns seamlessly with industry best practices.
Vision Implementation: Whether you have a specific vision in mind or are looking for inspiration, Robin is here to assist. He works closely with you to understand your aspirations, offering practical insights and actionable steps to turn your ideas into tangible results.
Comprehensive Assessment: Our onsite consults go beyond the surface, offering a thorough assessment of your current business operations. Robin meticulously examines existing processes, technologies, and workflows to identify areas for improvement and optimization.
Technology Tailoring: With a keen understanding of the latest technological advancements, Robin recommends solutions tailored to the unique needs of your company. Whether it's optimizing existing systems or introducing innovative technologies, he ensures that your business stays ahead of the curve.
Collaborative Approach: Robin fosters a collaborative environment, working closely with your team to implement changes seamlessly. His hands-on approach ensures that every member of your organization is equipped to adapt to and embrace new technologies effectively.
By choosing our onsite consulting services, you're not just getting a consultant; you're gaining a strategic partner dedicated to the success of your business. Robin's personalized approach and commitment to excellence make him an invaluable resource for businesses looking to thrive in today's dynamic landscape. Let us bring your vision to life and empower your company with the right technology solutions.

Cyber Security
Cybersecurity Services shield your network against threats and strengthen your cyber defenses.
Having the proper level of cyber security in place can prevent attacks and is apart of the mandated requirements for many business, banking and cyber insurance policies.
We can support your own Cyber Security program or we offer our own included in our MSP services.

Managed IT Service Provider

Desktop Support
We have a comprehensive understanding of computer hardware and software, including operating systems, networking and security.
Desktop support able to diagnose and troubleshoot computer and network problems. Remote or on-site, we have you covered.

AutoCAD
AutoCAD has its own beefier system requirements and is used across many different industries.
Unfortunately we see many businesses sold the wrong computer to host this program and are upsold to more system than they needed. We have our own hardware vendors, giving you the power you need to get the job done with a custom system without the 'designer' prices.

Computer Systems
Computer systems are a lot like your car or home. You keep up on that maintenance and it will get you far.
Maintenance like blowing out the tower once a year and actively monitoring for overheating or other system stressors can extend the life of your systems.
When its time to upgrade, we expedite service. From data transfer to install, we handle the entire process. You have peace of mind knowing you bought a system that will handle your industry requirements and did not get upsold just for a sale.

Laptops
We all enjoy the convenience of tech that can travel. Picking the right system that is durable and reliable is important. From docking stations, to cooling pads, there are ways to extend the life and quality of your laptop. Save yourself from the headache of shopping and comparing dozens of systems. We provide detailed quotes, pick up, drop off and data transfers.

Printers
Paper, PDF or 3D wood printers, we work with a lot of printers in different applications.
Whether you need assistance navigating a contracted agreement with your established printer vendor to setting up Sue so she stops manually punching in her entire email at the printer every time she scans something, we can handle it.

Office Move
Rearranging the office? Relocating to a new location?
Pre-move we can pack up the systems keeping them organized. Nothing is worse that having a monitor adapter go missing.
New space? Do you need line drops? Where is the router going? Is there power in the proper spaces? We look at many different aspects of the space to verify you have the right setup.

Onboarding / Offboarding
Staffing shifts can create a lot of items that need to happen in a timely manner.
Adding a new user to an identity management system or removing a user's privileges. Introducing new devices within an organization that are connected to the company network. We can handle that.
Emails
A vital part of communication, when email goes down, often panic ensues.
From assisting that one employee learn the ways of auto archive to stopping a email phishing attack, we have done it all.
Let us get you back up and flowing.

The Hub of Emails
With an Exchange Server you are able to create, monitor and store emails in a central location.
All emails are sent to the Server first. From there they are picked up by the computer. This process allows for emails to be stored and scanned to keep the overall network safe from breaches.

Malware Extortion
Ransomeware is a form of malware that is designed to encrypt files on a device, rendering them unusable.
Often bad actors will then demand ransom to release the files. Ransomeware can be picked up from emails, bad links, or infected websites. With the right software this can be deterred.
The best protection comes from educating users and keeping potentially unsecured sites blocked.

Also Known as Exchange Server
With an Exchange Server you are able to create, monitor and store emails in a central location. All emails are sent to the Server first. From there they are picked up by the computer. This process allows for emails to be stored and scanned to keep keep the overall network safe from infections.

Cloud Services
When most people think of the cloud they think of their server or back ups being in the cloud.
This could also include VPN services and Database storage.
We can assist you with managing your own cloud services. You can keep ownership of these cloud services and simply allow us assess to support them.
Should you ever wish to terminate that link, it is as easy as clicking a button. All resources stay with you. We pride ourselves on this because no one should ever feel their information is being held hostage by a hacker or a provider.

Ergonomics
What is ergonomics? Ergonomics can roughly be defined as the study of people in their working environment. More specifically, an ergonomist designs or modifies the work to fit the worker, not the other way around. The goal is to eliminate discomfort and risk of injury due to work.

Support from a distance
Remote support software enables IT technicians to access another computer or device remotely to provide support. The remote connection allows the technician to see the screen of the remote device on their own screen in real-time, and in most cases be able to take control of the remote device to troubleshoot issues and perform other tasks.

Software Support
We are able to assist you with programs such as AutoCAD, QuickBooks, and Microsoft.
We can assist you with managing your own software services and subscriptions. You keep ownership of these services and simply allow us to support them.
Should you ever wish to terminate that link, it is as easy as clicking a button. All resources stay with you. We pride ourselves on this because no one should ever feel their information is being held hostage by a hacker or a provider.

Network Infrastructure Audit
An IT audit provides an overview of your current network and vulnerabilities.
Hardware
Applications & Virtual Servers
Cloud Services
Backups
Cyber Security
Previous Services Provided
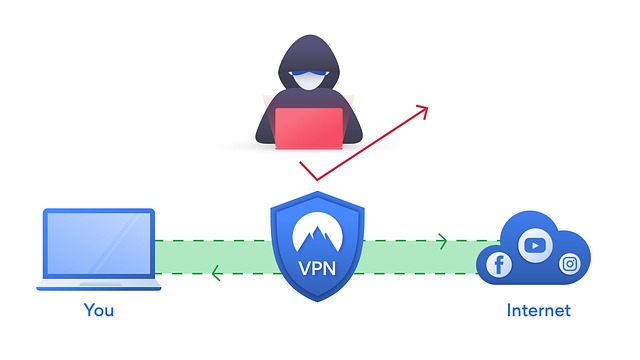
Secure Remote Access
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.

Hardware
Computer hardware includes the physical parts of a computer, such as the case, central processing unit (CPU), random access memory (RAM), monitor, mouse, keyboard, computer data storage, graphics card, sound card, speakers and motherboard.
We offer quotes and competitive pricing.

HIPAA Compliance
The Health Insurance Portability and Accountability Act (HIPAA) sets the standard for sensitive patient data protection. Companies that deal with protected health information (PHI) must have physical, network, and process security measures in place and follow them to ensure HIPAA Compliance.
After a fifteen year career traveling all over the US to service medical offices and hospitals, we like to think we know a little bit about HIPPA Compliance.

Network
A network is a group of two or more computers or other electronic devices that are interconnected for the purpose of exchanging data and sharing resources.
Looking to review your network or expand it? Let's take a look.

Router
A router is a device that allows for multiple devices to use the same internet connection. These can also allow for a stronger broadcast of your network over Wi-Fi where the provider modem may not offer the ability.
There are other options for boosting a Wi-Fi signal.
- Check Your Wired Internet Connection
- Update Your Router Firmware
- Achieve Optimal Router Placement
- Check Frequency
- Change Channel
- Kick Off Wi-Fi Intruders
- Control What's Being Used On The Network *Blocking Unwanted Sites
- Replace Your Antenna
- Upgrade Obsolete Hardware
- Reach Further With a Range Extender or Mesh Wi-Fi

World Wide Web
The Internet is a global system of interconnected computer networks that uses the Internet protocol suite to communicate between networks and devices. It is a network of networks that consists of private, public, academic, business, and government networks of local to global scope, linked by a broad array of electronic, wireless, and optical networking technologies. The Internet carries a vast range of information resources and services, such as the interlinked hypertext documents and applications of the World Wide Web (WWW), electronic mail, telephony, and file sharing.
There can be many points of failure causing slow internet or weak signals. We can assist you in checking that you are getting the level of service promised and verify you are on the best level of service for your needs that can be provided in your area.

First Line of Defense
A Firewall is a network security device or software that monitors and filters incoming and outgoing network traffic based on an organization's previously established security policies. At its most basic, a firewall is essentially the barrier that sits between a private internal network and the public Internet.

Vendor Compliance
Do you have a new vendor that has a list of requirements for your network to bring it into compliance?
Renewing your Business Insurance Policy and adding on that Cyber liability package this year? That form to apply has a lot of questions only your IT team is going to know. Plus, we can verify you have certain security measures in place to help lower that rate.
Are you working with your Banking entity after a breach to restore the ability to do banking for your Business accounts?
Often you don't even know about them until you are faced with these situations. We can assist you and guide you through it.

PC Virus
A computer virus is a type of computer program that, when executed, replicates itself by modifying other computer programs and inserting its own code into those programs. If this replication succeeds, the affected areas are then said to be "infected" with a computer virus, a metaphor derived from biological viruses. Software can prevent this, as can user awareness on Cyber defense.
Often detrimental viruses breach a company and seed tracking algorithms to collect data. Months later they are checked to verify the vulnerabilities are still there and use the collected information to coordinate an aggressive attack.

The Human Element
The most efficient way to educate your employees on how to fortify the human element of your company's security is through cybersecurity awareness training. For remote workers in particular, phishing, social engineering, compromised passwords and weak network security can expose your business to attackers.
To keep employees fresh on how to protect themselves online, and make them aware of new, emerging threats and attack techniques, it's recommended that training be completed at least once a year. Many business compliance or insurance requirements also mandate annual training.

What is an external hard drive for?

Recover the unrecoverable
When drives fail and are no longer usable by the computer. There is still the chance that data could be recovered from the physical disks. Through specialized workspace and software we are able to recover information as long as the physical drives are not broken.
